The Needle Roller Bearing is a Roller Bearing with a cylindrical roller. Relative to its diameter, the roller is both thin and long. This roller is called a Needle Roller. Although it has a small section, the load bearing capacity of the bearing is still high, with thin and long Needle Bearing roller (roller diameter of D = 5mm, L/D = 2.5, L roller length), so the radial structure is compact, the minimum diameter of the diameter and load capacity and other types of bearings, bearing the same, especially for the structure in radial installation size limited.
According to the use of different occasions, can choose the inner ring of the bearing or needle roller and cage assembly, the shaft neck surface and the surface of shell holes matched with a bearing directly as the bearing inner and outer rolling surface, in order to ensure the load capacity and operating performance and have the same ring bearing, shaft or housing bore raceway surface hardness the machining precision and the surface quality of bearing ring raceway and similar. This kind of bearing can only bear radial load.
Needle Bearing Needle Bearing,Needle Roller Bearing Sizes,Needle Roller,Needle Roller Bearing LUOYANG AUTO BEARING CO.,LTD , https://www.ballbearing.nl
1, hidden SSID number SSID (hidden service set identifier) ​​can generally be obtained through the terminal scan, wireless bridge supports hidden service set identifier (SSID), that is, the device does not broadcast SSID, so the wireless terminal can not automatically scan to obtain the SSID, the terminal must Proactively provide the correct SSID number to associate with the wireless bridge. Therefore, we only need to hide the SSID number and there is no way to scan the SSID number we use. There is no way to directly establish a connection with our wireless bridge.
2. WEP (Wired Equivalent Privacy Mechanism). The wireless network implements the encryption mechanism based on the shared key in the 802.11 protocol. It is called the "Wired Equivalent Privacy" technology. WEP is an RC-4 based algorithm. 40bit or 128bit encryption technology. The mobile terminal and the wireless router can be configured with 4 sets of WEP keys, which can be used in turn for encrypting and transmitting data, allowing the encryption keys to change dynamically. High encryption level, basically meet the needs of ordinary business users.
To ensure the security of data transmission, a group of devices that communicate with each other, the encryption algorithm, and the encrypted content must be the same, otherwise communication cannot be performed normally. This is our most common form of encryption.
3. MAC address filtering MAC (physical address filtering control) uses a hardware control mechanism to implement the identification of accessing wireless terminals. Because the network card of the wireless terminal has a unique MAC address, if the MAC address filtering mechanism is enabled, the bridge cannot be allowed to communicate with the terminal only when the MAC address of the client is valid. In other words, the devices that communicate with each other can bind their MAC addresses to each other. The device only allows the devices that exist in the MAC address list to communicate with each other.
Specifically how to achieve the wireless bridge encryption, please call Shenzhen Laien technology and technical personnel, we have professional and technical personnel for your guidance. 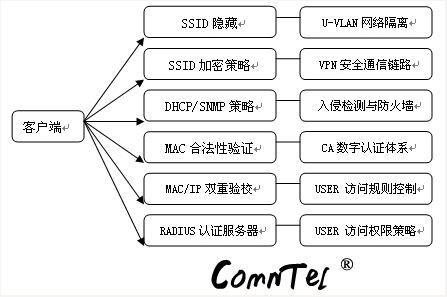


How Wireless Bridges Are Encrypted in Wireless Surveillance Systems
With the ever-increasing popularity of wireless signals, every time we use a mobile phone, we will find many wireless signals nearby. It can be seen that wireless is not only widely used in the field of surveillance, but also indispensable in our lives. In wireless monitoring, the wireless bridge adopts the transparent protocol. Therefore, the security of the wireless bridge is very poor. We must encrypt the wireless bridge when building the wireless monitoring system. After our wireless bridge is installed, we often find that there are some unfamiliar accounts in the wireless bridge connection. It may be that some people have cracked the password of your wireless bridge through some software, which will cause you to transmit the content. Leak MI. Therefore, in order to better ensure the stable transmission of our wireless signals, in order to protect personal privacy, encryption of wireless bridges is essential. So what kind of encryption methods does the wireless network technology of Shenzhen Leian technology produce?
